BANKING IS BELIEVING
News & Events
Security
LastPass Password Manager Breach
LastPass, the world’s most popular password manager, was breached twice in 2022. The second breach led to bad actors obtaining encrypted copies of users’ vault data – which includes usernames and passwords. Although the encryption applied to these vaults is very strong, it is not invulnerable. What to do? Enable multi-factor authentication everywhere it is...
Security
Keeping a Watchful Eye During the Holidays
You decided to brave the holiday crowds. You’ve been waiting in line for hours to purchase a must-have gift, finally make it to the checkout to pay, and the transaction is declined. GASP! What? How!? A call to the card issuer reveals that your information has been stolen, and your account has been maxed out....
Security
Cybercrime This Holiday Season
This holiday season, use caution when shopping online. Be wary of these common holiday scams. Remember to always think before you click. Too-Good-To-Be-True Sales & Deals If you’re like many holiday shoppers looking for a good deal on gifts, remember to avoid any sales that seem too-good-to-be-true (because they probably are). Phishing emails or ads...
Security
How Fraudsters Are Exploiting Digital Platforms with Creative Phishing Scams
In an increasingly digital world, phishing scams are becoming more prevalent. The fraudsters behind these scams are finding more creative ways to exploit digital platforms like email, text, phone and peer-to-peer (P2P) payment apps. According to the Federal Trade Commission’s report on fraud, it’s estimated that American consumers lost a staggering $5.8 billion to phishing...
Security
Protect Yourself from Peer-to-Peer (P2P) Related Fraud
Peer-to-peer (P2P) payment apps such as Zelle, Venmo and CashApp enable users to conveniently send money directly to another user — and fraudsters aren’t afraid of exploiting them. P2P related fraud has been increasing over the last few years. With bad actors are finding very creative ways to exploit these P2P payment apps with phishing/smishing/vishing...
Security
Beware of Amazon Prime Day Scammers
Amazon Prime Days brings discounted prices along with new phishing scams from cybercriminals looking for any opportunity to capitalize. Phishing emails using the Amazon brand to add legitimacy top the list, but scams involving text messages and even phone calls saying they are from Amazon have been reported. These scams take into consideration the huge...
Security
Account Alerts
Account and Service alerts provide real-time updates on a variety of account activities to better manage your finances. Choose to receive email or text alerts – they’re user-friendly and help you keep track of money moving in and out of your accounts to prevent overdrafts, avoid fraud and keep a closer eye on your finances....
What's New
Positive Pay can protect you from check fraud losses
Please be aware that we’ve recently seen an uptick in business check fraud, mainly from unattended mail. It’s important to have either a P.O. Box or direct delivery inside an office. If a criminal gets a hold of your checks, they’ve now obtained private business information, which not only allows them to alter your checks,...
Security
Gift Card Scams
Scammers who ask for payment in gift cards often impersonate a well-known business or government agency, commonly with promises of tech or security support, which can be convincing. If you receive a call from someone claiming to be from Microsoft offering to help fix your infected computer for $200 in Target gift cards, that’s a...
Security
How to Spot a Phishing Scam
Phishing is the fraudulent attempt to obtain sensitive, personal information such as usernames, passwords, credit card numbers or account information by posing as a trustworthy source, such as a reputable company. Phishing is commonly done through email, although social networking sites and chatting apps are becoming increasingly common routes as well. How to spot a...
Security
Know The Signs of Business Email Compromise
You receive an email from a customer asking you to complete a Request for Proposal (RFP), or view a secure document. The request came from someone you’ve dealt with before, but you weren’t expecting this request. The sender looks right, and your email filter didn’t block it, but who is in control of the sender’s...
Security
How To Increase Your Business Cybersecurity
Nearly half of all cyberattacks target small businesses. Yet only 40% of small businesses have a cybersecurity policy. Security breaches surged in the pandemic as more employees worked remotely, making data even more accessible to cybercriminals. As businesses work to recover from the COVID-19 pandemic, their vulnerability to fraud is at an all-time high. Just...
Security
Beware Of Text Messages Claiming That Your Debit Card Has Been Locked
Phishing text messages are becoming an increasingly common method for fraudsters to gain access to confidential information. Be on the lookout for text messages that claim your debit card is locked or has been blocked due to a recent transaction and ask you to respond if the activity is authorized or not, as shown in...
Security
Protect Yourself From Tax Fraud
As tax season ramps up, so does tax-related fraud. Know what to look for, and take steps to protect sensitive information. SPOTTING TAX FRAUD Phone Calls: The IRS will never notify you of a tax issue by phone until it has first sent written notification, usually multiple times. If a caller claims to be from...
Security
Should A Company Pay A Ransom?
Ransomware attackers specialize in penetrating corporate networks, and sometimes specifically target a business’ backup systems, making it difficult – or impossible – to remediate the harm of an attack. The frequency and size of ransomware incidents have increased significantly in recent years. No company is safe from being targeted. How You Can Help Protect Your Business...
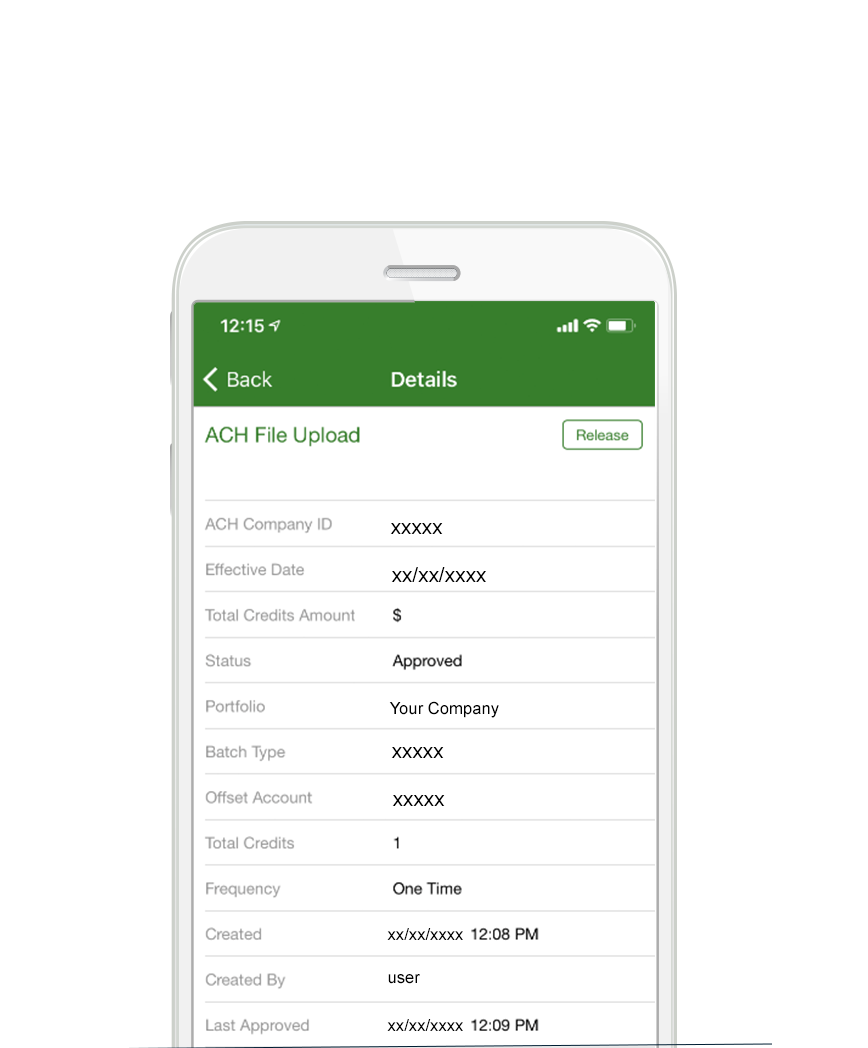
Security
Approve ACH or Wire Payments On-The-Go
With on-the-go approval, it’s more convenient than ever to utilize dual control and increase your business account security. Authorized users can quickly and easily approve or release payments from anywhere with the GSB mobile app. Requiring a second approver for ACH originations and wire transfers will give you peace of mind and help protect your...
Security
SBA PPP Borrower Data Publicly Released
Third-party businesses are using information from a court-ordered public release of Small Business Administration (SBA) Paycheck Protection Program (PPP) borrowers to deceptively market themselves. Their communications may reference Gorham Savings Bank and may even imply that we have an affiliation. Please be aware that we will communicate directly with you about your PPP loan and...
Security
SBA COVID-19 Relief Scams and Fraud Alerts
Please be aware of a variety of malicious attempts by cyber-criminals taking advantage of the Small Business Administration (SBA)’s COVID-19 relief efforts to gather sensitive information and steal funds from businesses. Always think before you click! Grants/Loans The SBA does not initiate contact on either loans or grants. If you are proactively contacted by someone...
Security
Unemployment Insurance Program Targeted by Fraudsters
The US Secret Service is warning of a well-organized fraud ring exploiting the COVID-19 crisis in order to commit large-scale fraud against state unemployment insurance programs. Individuals are receiving multiple deposits from various State Unemployment Benefit Programs. It is assumed the fraud ring behind this possesses a substantial database of Personally Identifiable Information (PII) in...
Security
Beware of COVID-19 Scams Using the FDIC’s Name
During these unprecedented times scammers are using false information regarding the security of people’s deposits or their ability to access cash to perpetuate fraud schemes. The FDIC does not send unsolicited correspondence asking for money or sensitive personal information. The agency will never contact you to ask for personal details, such as bank account information,...
Security
Coronavirus Phishing Scams
Beware of COVID-19 emails that appear to come from reputable sources, such as the Centers for Disease Control (CDC) and World Health Organization (WHO). The body of these emails often contain recent news and updates related to the Coronavirus. These emails ask you to click on links for more detailed information – but actually link...
Security
Recent Business Fraud Activity
The following types of business fraud have been on the rise. As always, we encourage you to be on the lookout – and to be diligent in your verification process. Wire Fraud We’ve seen an increase in business wire fraud from criminals intercepting valid wire request emails and altering the payment instructions. Never wire money...
Security
How To Secure Your Smart Devices
Smart devices are everywhere these days and it’s likely that you own several (Amazon Alexa, Nest, Google Home, just to name a few). Like all internet-connected technology, smart devices are vulnerable to being hacked, so steps should be taken to secure them. Here are some simple steps: Setup Passwords: Many smart devices come with a...
Security
How to Recognize a Phone Scam
Phone scams come in many forms, but they are easy to spot if you know what to look for. Note: If your phone is listed on the National Do Not Call Registry it is illegal for a company to call you. If a company is already breaking the law, there is a good chance it’s...
Security
Tips for Spotting and Avoiding Check Fraud
Fake checks come in many forms – you could receive a fraudulent check or your account information could be used to create fraudulent checks. Understanding how check processing works and how to keep your information secure can help safeguard you from this type of activity. Check fraud can come in a variety of forms: Counterfeit...
Security
Tips For Monitoring Your Financial Accounts
Monitoring your account activity is one of the most effective ways to protect yourself from fraud. The sooner you are able to identify unauthorized activity, the better you can take action to reduce the impact. Here are some tips for monitoring your accounts and credit. Monitoring Your Accounts Review account activity often, daily if possible,...
Security
Spotting and Preventing Wire Fraud
Fraudulent wire activity is generally a result of account takeovers and email compromises. This form of fraud can be difficult to detect because they use a valid email address, craft their communication to mimic the owners, and add urgency to their request(s). Sometimes payment is expected from the recipient and the communication channel may have...
Security
Signs of Elder Financial Abuse
Many elderly people are targets of financial exploitation because they are likely to have savings accounts, fixed incomes, receive social security benefits or own their homes. Sadly, many who are financially exploited experience this abuse at the hands of trusted caregivers or family members. This can make the victim feel heartbroken, embarrassed and ashamed. They...
Security
Social Security Is Not Trying To Take Your Benefits
Scammers are making calls posing as someone from the Social Security Administration and telling people that their Social Security Number or Benefits will be suspended. The goal of this scam is to convince people to send money, often in the form of gift cards. What to do: Hang up – do not answer any questions...
Security
Beware of Fake Equifax Data Breach Settlement Websites
The Equifax Breach, and subsequent settlement, has received a lot of media attention. Scammers are seizing this opportunity to establish fake settlement sites. Don’t follow email links or web search results. Refer to the FTC’s website for claim information, including officially approved links: www.ftc.gov/Equifax Scam Calls, Texts, and Emails Scammers are making calls and sending...